Computers have become an integral part of our day to day lives, especially for business owners. Access to the internet gives people in developing countries the opportunity to access global economies for the buying and selling of goods. This access, in turn, allows them access to opportunities that may not exist in their home countries.
Here, the idea of cashless transactions does make sense. Someone based in the United States, for example, is not going to send a wad of cash over to Ghana to purchase goods. It’s a simple enough solution to send money through PayPal, or the blockchain, but again, you run the risk of being attacked by cyber-criminals.
What to Do?
So, it is something of a catch-22 situation. To be a player in global markets, and access this sort of funding, cashless transactions are essential. But how do you ensure that you are not a target of cyber-criminals? We will look at that in this post.
Start with Anti-Virus Software and Encryption
As a business owner of any kind, your data is one of the most important assets that your business has. It is also this data that hackers most want to get their hands on. If you store the personal details for your clients, it is essential to keep this data secure.
Start by installing a top-rate anti-virus program. Schedule scans regularly and keep these programs completely up to date.
Next, use an encryption program to add another layer of security to the files. That way, even if someone does gain access to your computer, they have another level of security to deal with to get the information in the file.
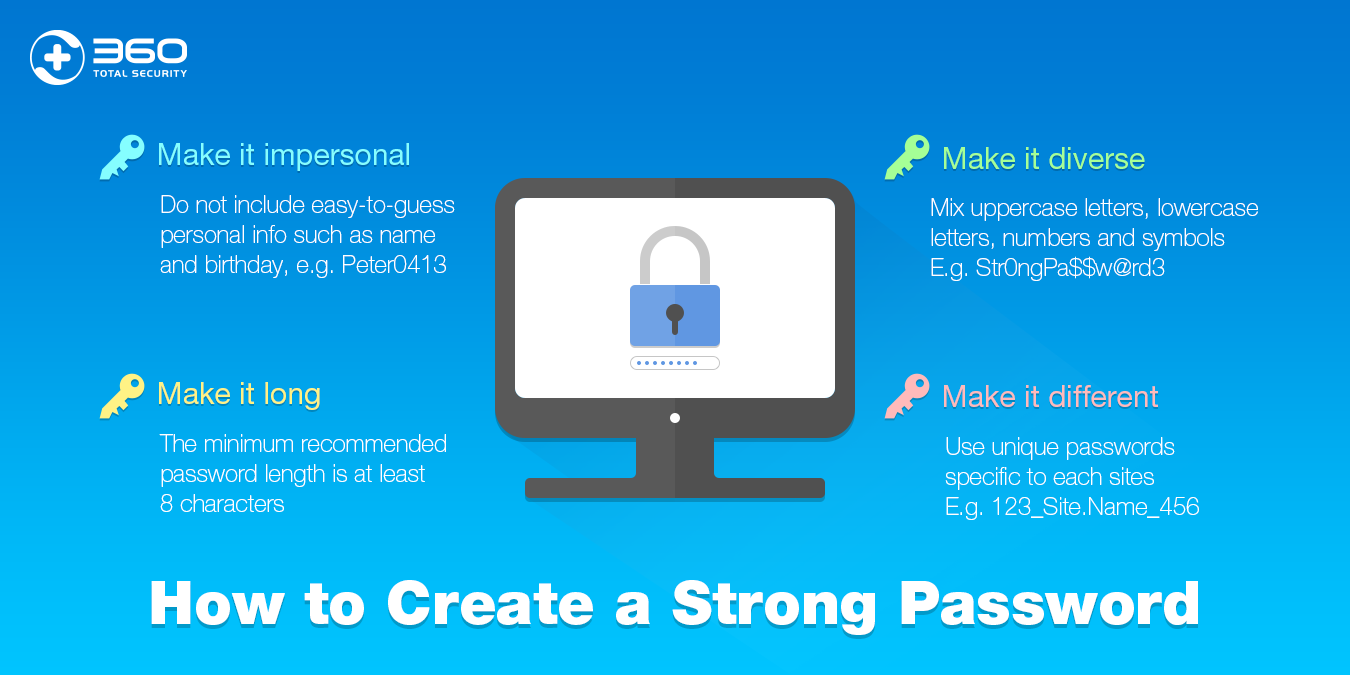
Use Strong Passwords
This is something that we all should do anyway, but many of us don’t. Making your passwords longer and keeping away from common phrases or words helps to keep your data more secure. Here are ways to make your password harder to crack:
- Longer is better than shorter. Think in terms of eight to twelve characters or more.
- Mix in uppercase and lowercase letters.
- Add alpha and numeric characters.
- Throw in a special character or two as well.
- Don’t use common phrases or any phrase that someone might be able to guess. So, your child’s first name, pet’s name, birthdays, etc. are all out.
The stronger your password, the longer it will take to crack it. Don’t use the same password that you use elsewhere and do change the password at least once a month.
Protect Against Ransomware
This is a relatively new form of cyber attack and one of the more aggressive forms. It can cripple your business. It is simple – a hacker gains access to your computer and locks you out. If you want to regain access, you have to pay a fee to the hacker and hope that they will give you the password.
Your best defense here is to have a high-quality anti-ransomware program installed and to ensure that all your data is backed up on a regular basis. If the data is backed up, you will have some way of accessing it on a different computer.
It might also be an idea to keep your customer details in cold storage instead of on your computer. This means backing the information up on a computer that never has access to the internet, or to an external hard drive.
Educate your personnel
30% of phishing messages get opened and 12% of those users click on the malicious attachment or link. In case you have a software with real-time protection, it might deal with it instantly and warn the user. But in case not – user runs it and cybercriminals celebrate another successful attack. The solution for this is security awareness training that proves its efficiency day-by-day by minimizing overall security breaches. But remember – only complex of actions will make you as secured as possible.
Secure Your Website
If you have a website, it is important to secure it as well as possible to ensure that it is a more difficult target for hackers. Use strong passwords as discussed above, and change these regularly.
Keep the bare minimum of information about your client’s personal details on the site. So, if they need to Login to access their account with you, for example, keep only enough information on the site to allow this. All other information should be stored elsewhere.
Crypto-jacking
This is another form of hacking that is relatively new. And it furthers William Davis’s argument against cashless societies. This form of cyber-crime has come about as a direct result of introducing alternative payment methods. In this case, blockchain technology.
What happens is fairly simple. The hacker gains access to your site and then installs a script on the site. This script runs in the background. When someone visits the site, the script springs into action and the user’s computer is used to mine cryptocurrency.
The only indication that the visitor will have that something is amiss is that their computer slows down significantly due to this mining. It is very energy-intensive and uses a lot of power – both in terms of computing power and electricity consumption.
With the value of cryptos increasing in recent years, this has become a popular tactic. According to Malwarebytes, the problem is extensive. They present a small cross-section of information that they have gleaned from Coinhive that shows the monetary value of some of the funds raised.
Coinhive is a legitimate blockchain-based application that allows website owners to make money on their sites. Instead of being bombarded by ads, users will simply donate some of their computing power to mine cryptos. There are two versions – one that allows users to opt in, and another that runs silently.
As you will see from the usage statistics that Malwarebytes gleaned, the latter is far more popular, raising just under $2 million to $4 million a day over the period monitored. The opt-in version, by contrast, came in at a high of just over $100 thousand over the same period.
What makes this form of hacking so insidious is that they only have to infect your site to affect all of your visitors. That is why it is fundamentally important to ensure that your site is properly secured with a good anti-virus program and that you check it regularly for unfamiliar script.
In conclusion, there are several forms of cyber attack that a company may fall victim to. You are not completely helpless in the matter, though. If you practice sound security measures and make yourself as hard a target as possible, you will dissuade the majority of hackers.
Let’s dig into the infographic “Awesome cyber security facts”:



